
Backing-up is not hard to do
by Larry Magid This post first appeared in the Mercury News The most tragic consequence of the recent Maui fires is, of course, loss of life. There was also horrific property loss. What you don’t […]

by Larry Magid This post first appeared in the Mercury News The most tragic consequence of the recent Maui fires is, of course, loss of life. There was also horrific property loss. What you don’t […]

by Larry Magid This post first appeared in the Mercury News I was in the room in 2010 when Steve Jobs introduced the Apple iPad, and ever since then, Apple has pretty much dominated the […]

by Larry Magid That first 1983 column, “Learn Buzzwords Before Shopping,” described what were, at the time, unfamiliar terms like computer hardware, software, floppy disc, bite, kilobyte and megabyte. After defining what RAM (random access […]

Last week I bought a refrigerator. What was once a fairly easy buying decision can now be a lot more complicated thanks to feature creep and the inability to see many models on showroom floors. […]

I go for an annual checkup where a nurse checks my blood pressure, my oxygen saturation (Sp02), my weight, height and body temperature, followed by an exam and chat with my doctor. It’s an important […]

Now that the pandemic is theoretically over, a lot of people plan to travel this summer. While I don’t know of any apps that can remove traffic from the roads or diminish crowds at airports, […]
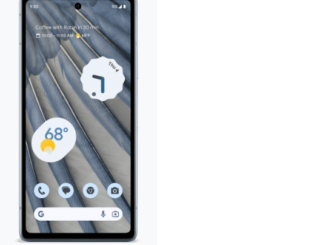
You know that adage, “you get what you pay for.” Well, it’s not always true. With Google’s new Pixel 7A phone, you get more than you pay for, compared with other phones. At $499, the […]

By Larry Magid A slightly shorter version of this post appeared in the Mercury News I was impacted by a scam this week that didn’t cost me money or expose my data, but did take an enormous […]
by Larry Magid This post is adapted from one that first appeared in the Mercury News We’re hearing a lot about the dangers of generative AI like ChatGPT, the new Microsoft Bing and Google Bard. For example, Geoffrey Hinton, who is often […]

By Larry Magid This post first appeared in the Mercury News Last week I wrote about a call I received claiming my wife had been kidnapped and demanding ransom. It came from a number that was nearly the same as […]
Copyright © 2024 | MH Magazine WordPress Theme by MH Themes